728x90
EKS 배포 방법
[VPC 생성 과정은 제외합니다.]
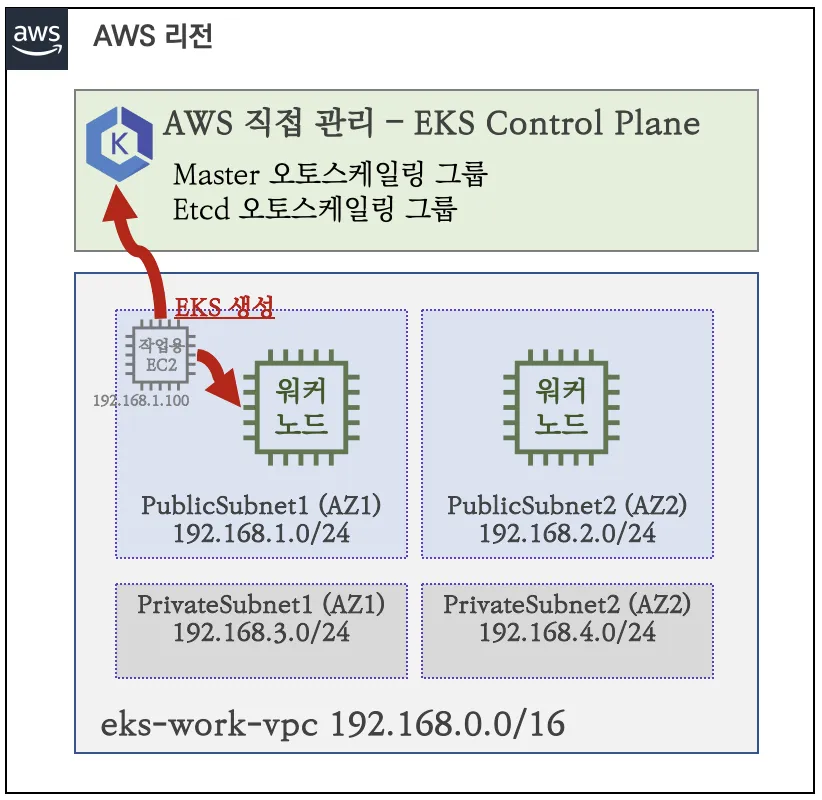
1. AWS 웹 콘솔을 통한 생성
- AWS EKS 메뉴 클릭 > 클러스터 생성 클릭
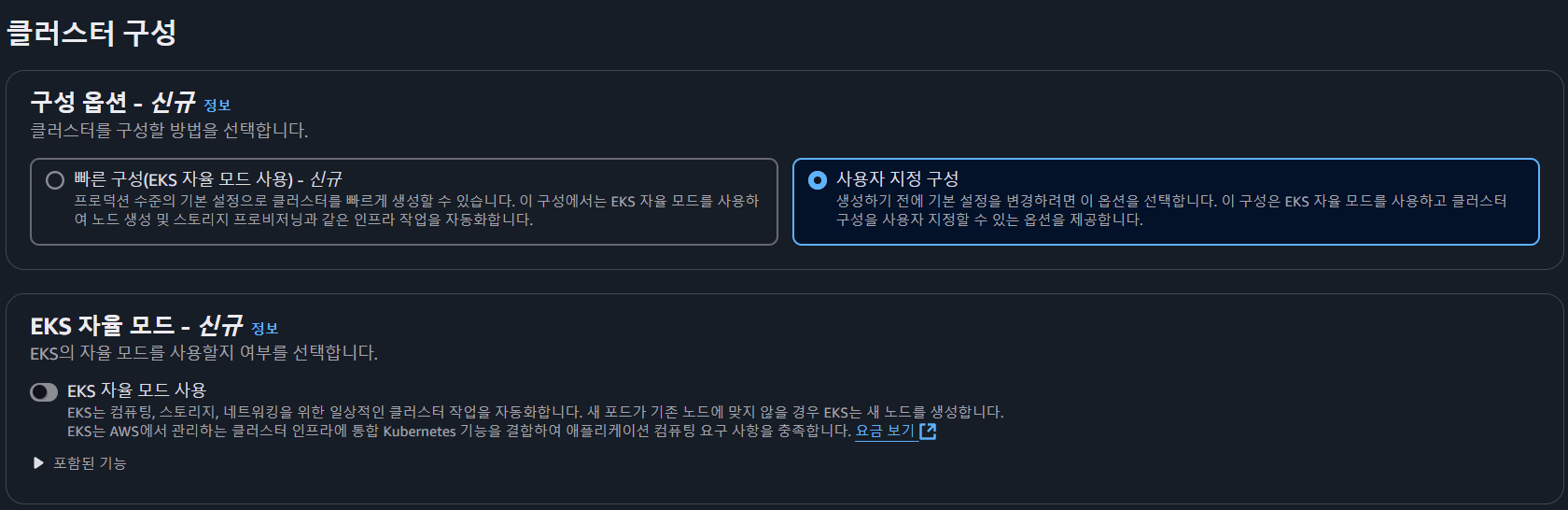
- 사용자 지정 구성 > EKS 자율 모드 사용 Disable (Auto mode)
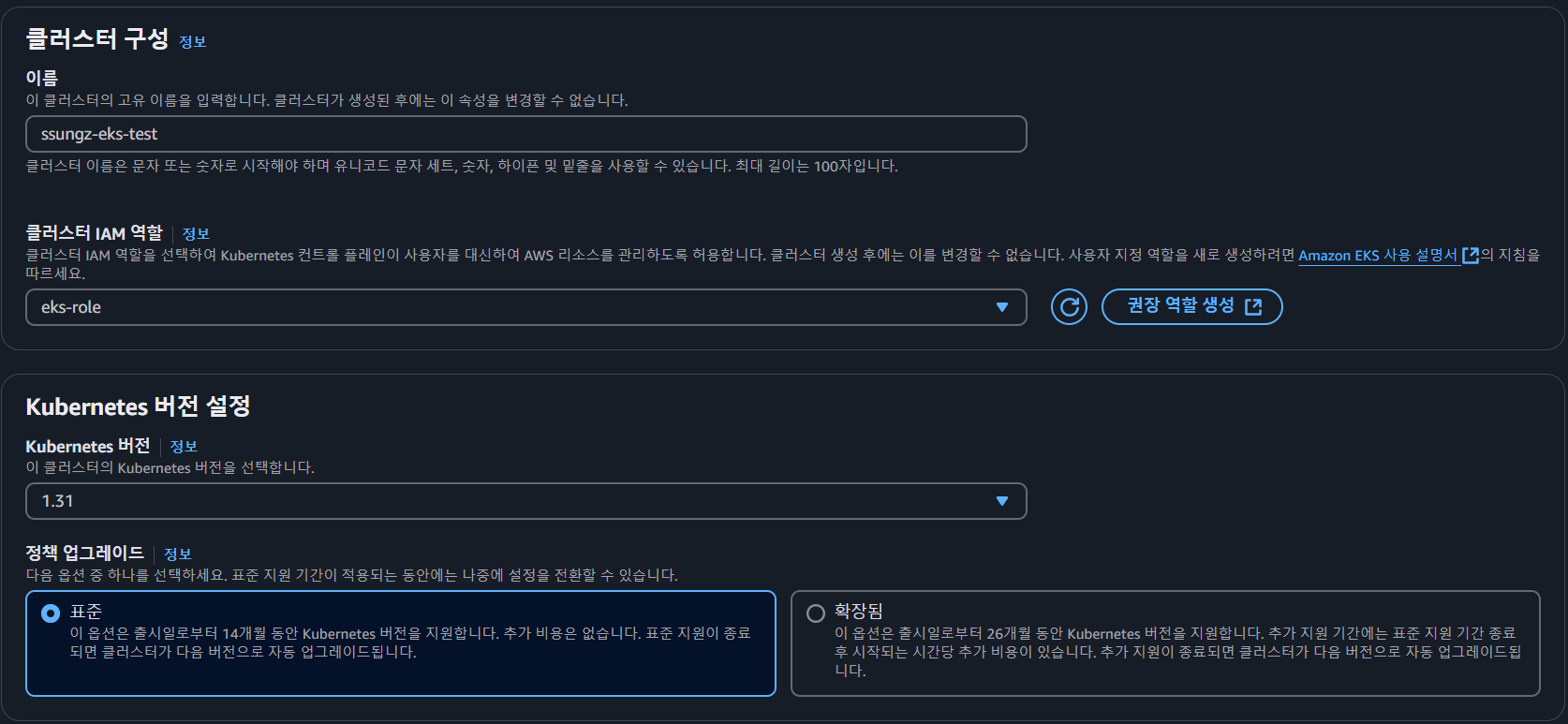
- Cluster 이름 작성 > Kubernetes 버전 지정
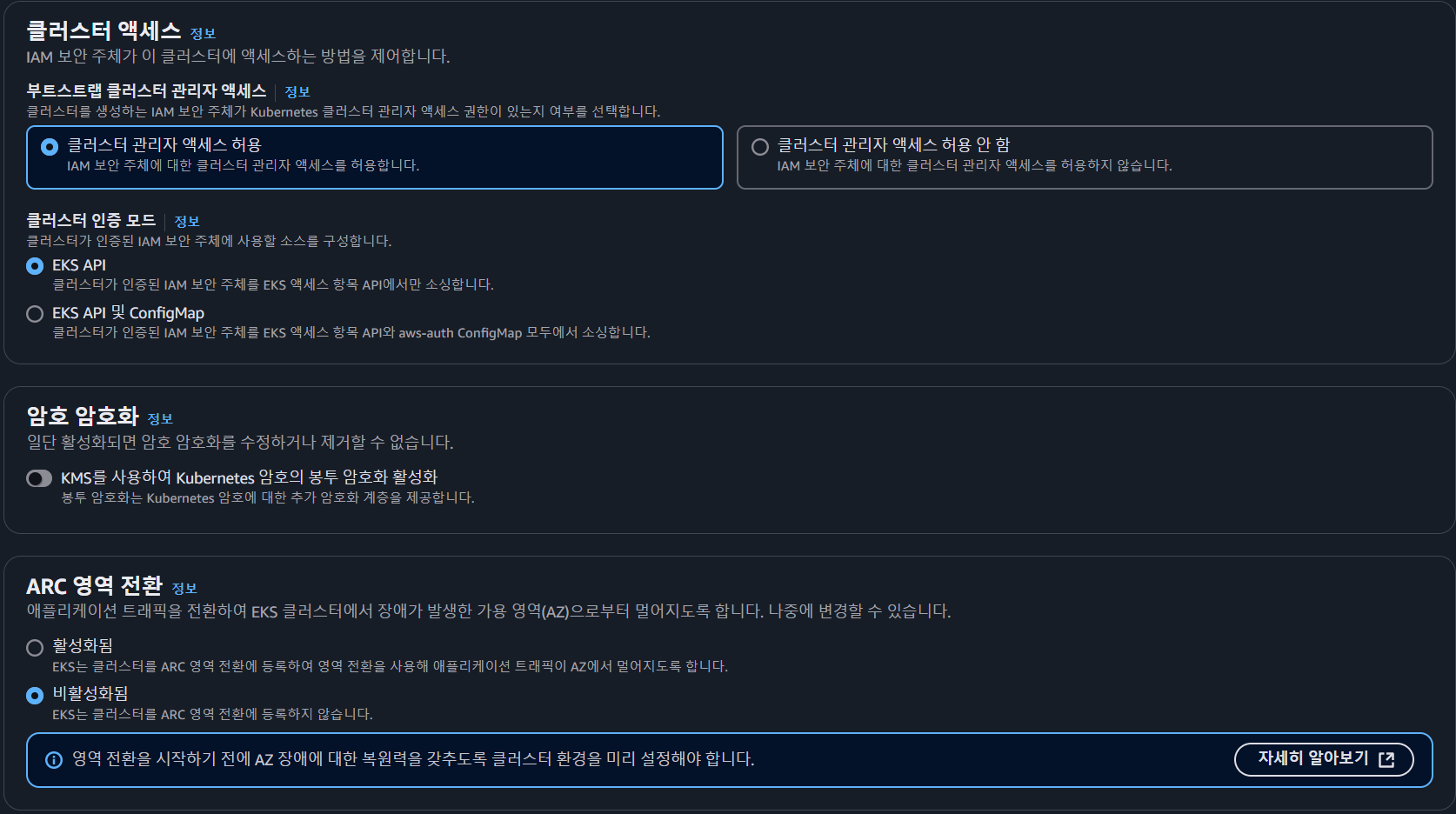
- 클러스터 액세스 방식 선택
- ARC 영역 전환 비활성화
- ARC 영역 전환은 크게 두가지로 나뉜다.
- 영역 이동(zonal shift) – 문제가 발생한 AZ에서 트래픽을 Healthy한 AZ로 신속하게 전환하여 문제를 임시로 해결
- 자동 영역 이동(zonal autoshift) – 연습 실행을 통해 미리 AZ 장애 시의 복구 상태를 점검하고 AWS가 복구 작업을 자동으로 처리할 수 있도록 설정
- ARC 영역 전환은 크게 두가지로 나뉜다.
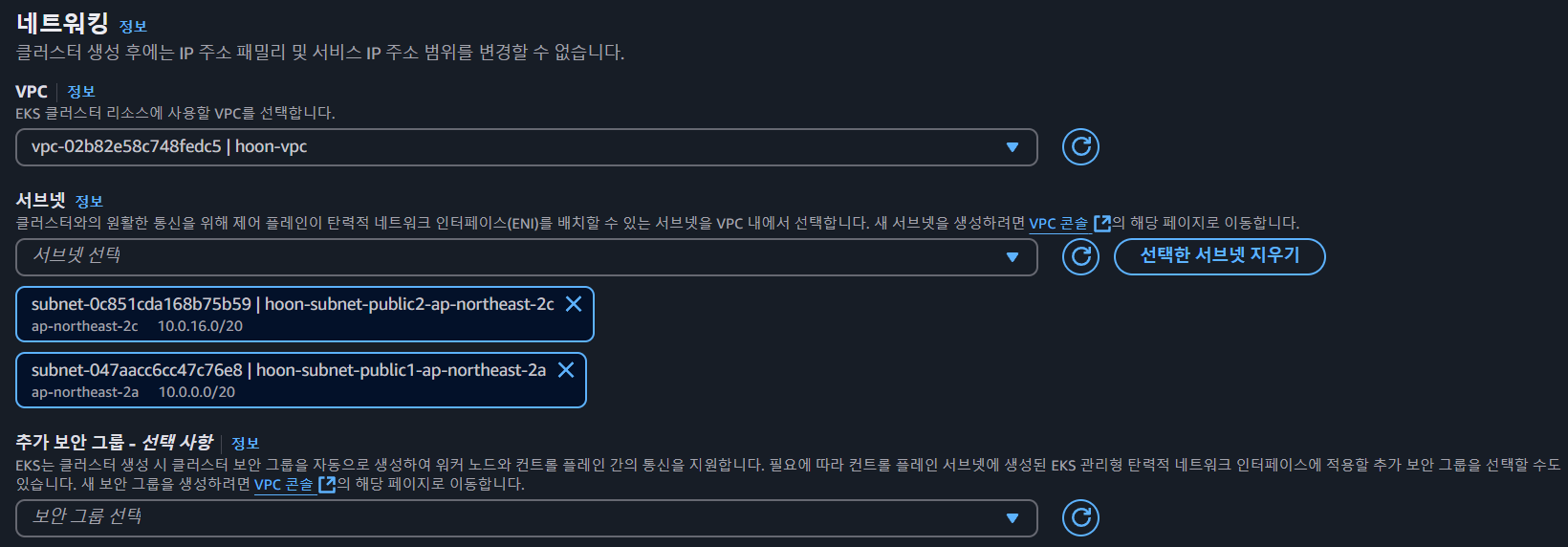
- 네트워킹 지정 (클러스터 엔드포인트 액세스는 Public으로 설정했습니다.)
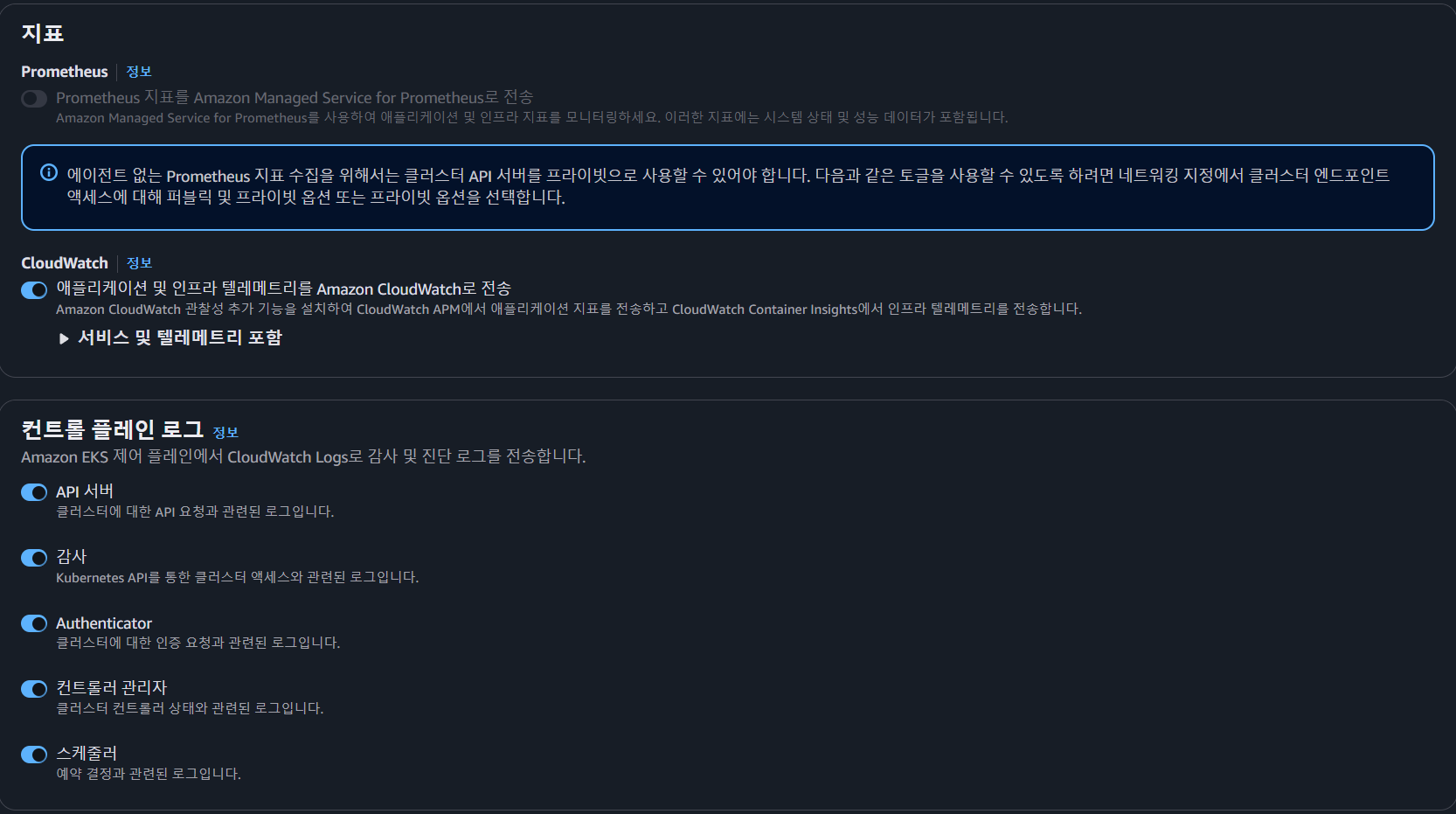
- 메트릭 설정
- (추가 기능 선택, 선택한 추가 기능 설정 구성)은 기본 값으로 설정했습니다.
- 검토 및 생성 - 설정한 값들이 잘 지정되어있는지 확인 후 생성합니다.
- 아래와 같이 생성이 완료되면 node group을 생성합니다.
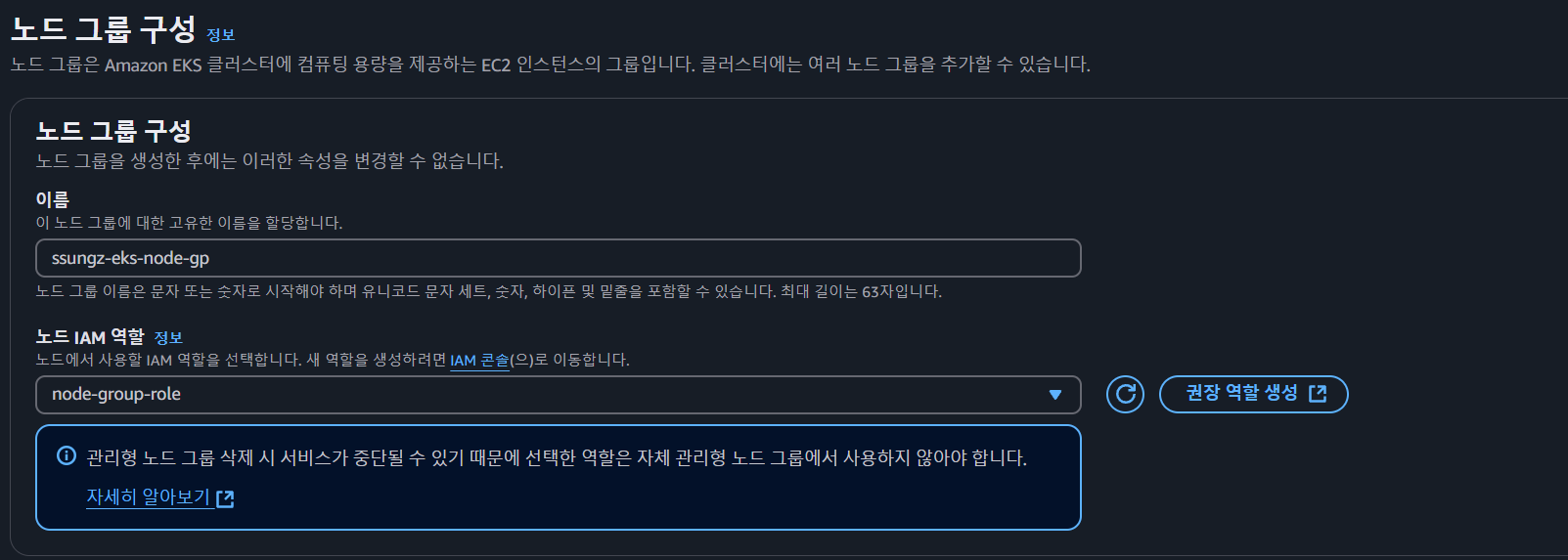
- node group 생성 (이름과 역할만 선택하고 나머지는 기본 값으로 설정했습니다.)
- node group에 소속될 인스턴스들의 OS와 Spec을 선택합니다. (나머지는 기본값으로 했습니다.)
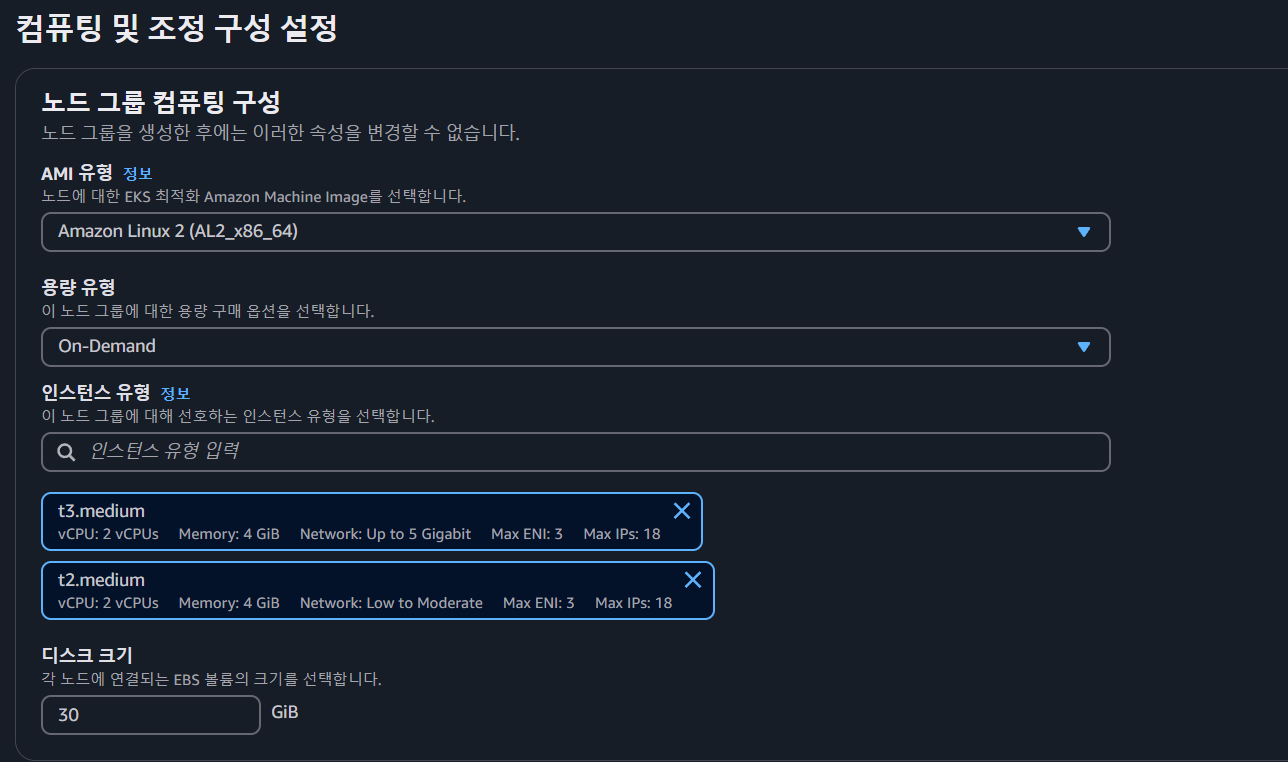
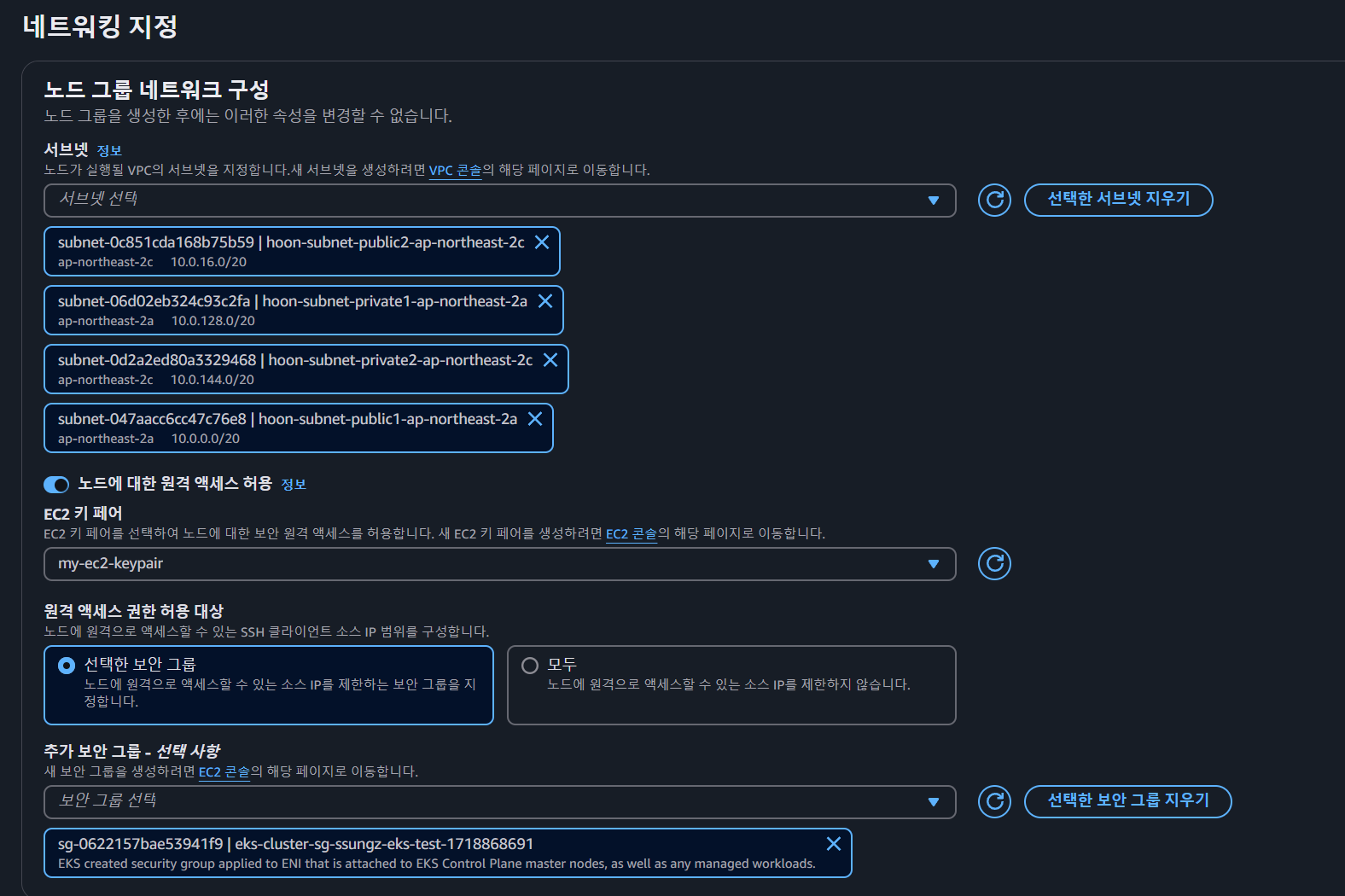
- 네트워크에 대한 설정도 기본 값으로 해줍니다.
- worker node에 원격 접속을 위해 ssh 허용을 설정합니다.
2. EKSCTL로 생성하는 방법 + bastion 서버
(CloudFormation으로 bastion 서버를 생성하고, bastion 서버 내에서 EKSCTL로 Cluster를 생성)
- CloudFormation Template 파일을 이용하여 VPC + Bastion 서버 생성
aws cloudformation deploy --template-file ./myeks-1week.yaml \
--stack-name myeks --parameter-overrides KeyName={KEY Pair Name} SgIngressSshCidr={자신의 IP} --region ap-northeast-2
## stack-name : CloudFormation에 등록할 stack 이름
## keyname : 자원 접속 시 사용할 key pair 이름
## SgIngressSshCidr : Security Group에 등록될 접근 IP
## region : 자원을 생성할 AWS 상의 Region
- 자원 생성 확인 (CloudFormation 상태 확인, VPC 리소스맵)
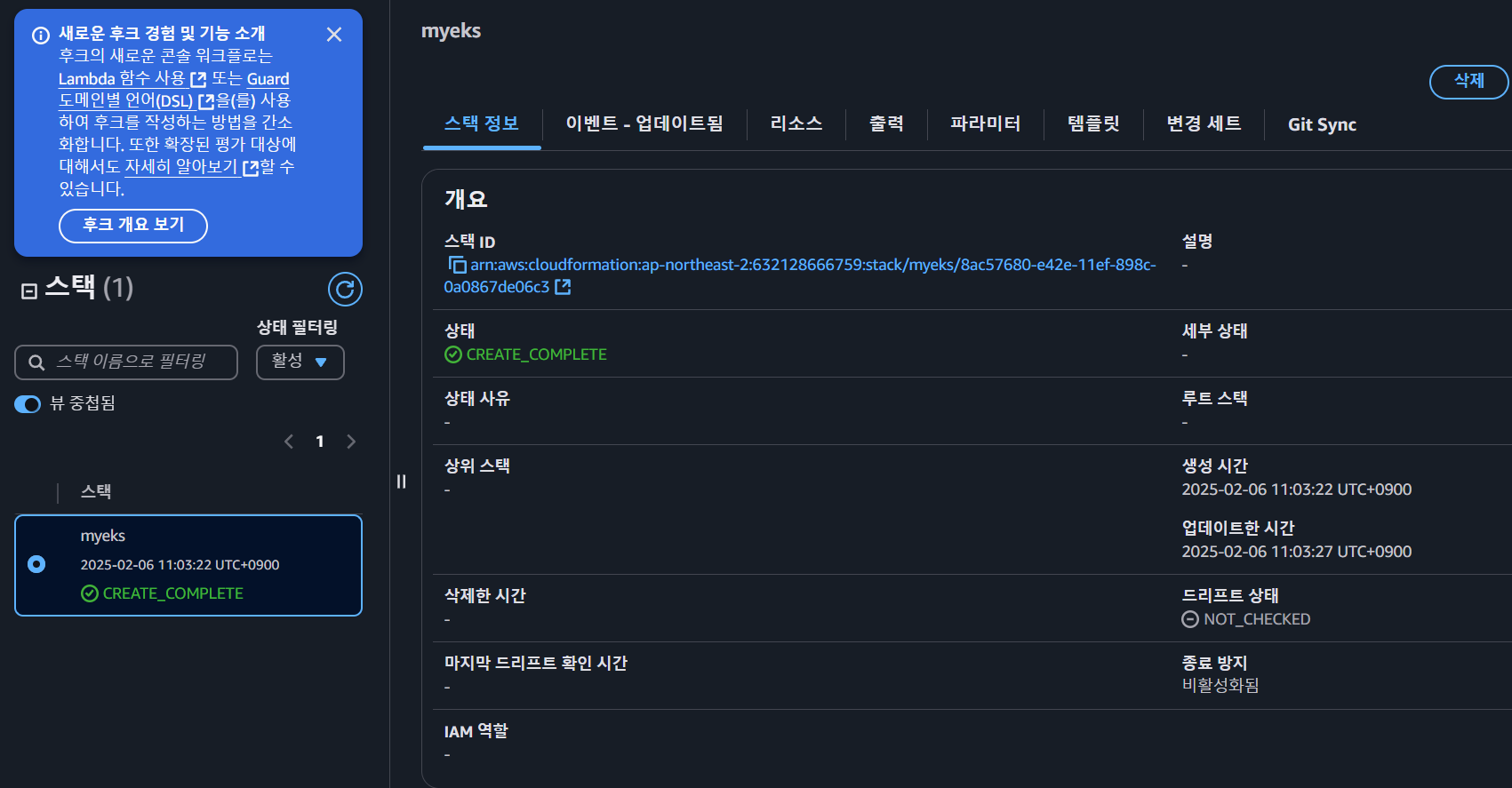
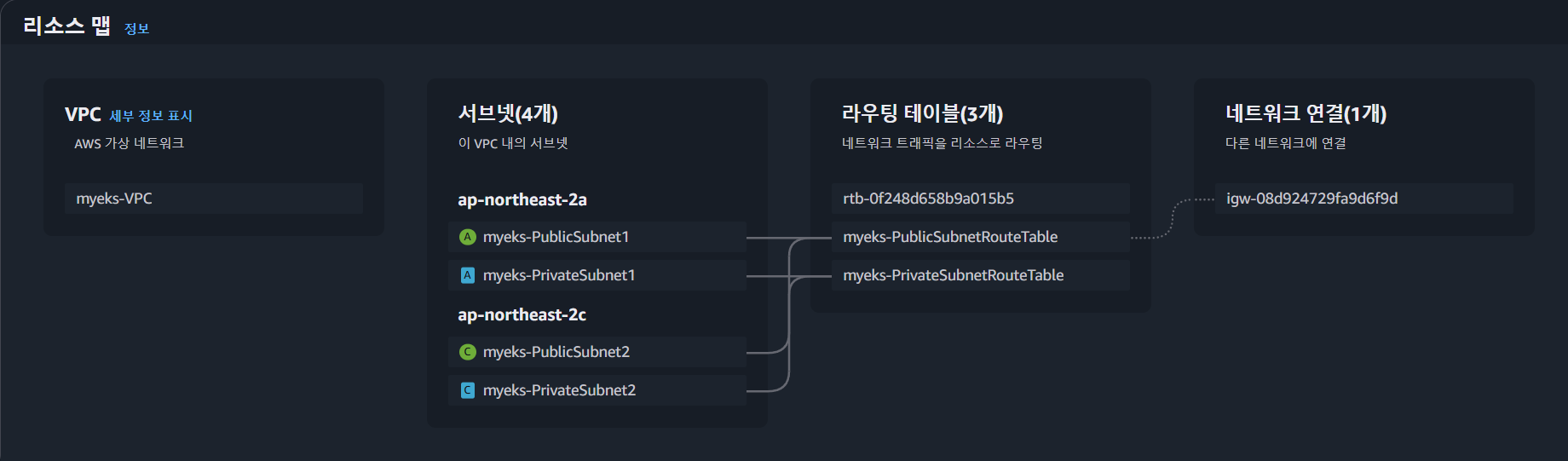
- Bastion 인스턴스 접속
ssh root@$(aws cloudformation describe-stacks --stack-name myeks --query 'Stacks[*].Outputs[0].OutputValue' --output text)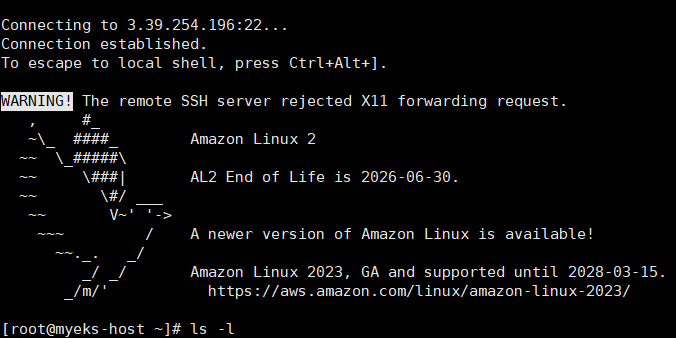
- Bastion 서버 내에 설치된 프로그램 정보 확인
## kubectl client 버전 확인
$ k version --client=true -o yaml
## eksctl 버전 확인
$ eksctl version
## aws cli 버전 확인
$ aws --version
==================================================
[root@myeks-host ~]# k version --client=true -o yaml
clientVersion:
buildDate: "2024-11-13T10:05:20Z"
compiler: gc
gitCommit: b3cca57dcb14f30db926fa1bd690e92ee5efdb82
gitTreeState: clean
gitVersion: v1.31.2-eks-94953ac
goVersion: go1.22.8
major: "1"
minor: 31+
platform: linux/amd64
kustomizeVersion: v5.4.2
[root@myeks-host ~]# eksctl version
0.203.0
[root@myeks-host ~]# aws --version
aws-cli/2.23.14 Python/3.12.6 Linux/4.14.355-275.582.amzn2.x86_64 exe/x86_64.amzn.2- AWS 자원 조회
- Bastion Instance
$ aws ec2 describe-instances --output table
|+----------------------------------------------------------+---------------------------------------------------------------------------------+|
||| Instances |||
||+--------------------------------------------+---------------------------------------------------------------------------------------------+||
||| AmiLaunchIndex | 0 |||
||| Architecture | x86_64 |||
||| ClientToken | fcd58613-fd73-aca7-7617-dd5989cd46a6 |||
||| CurrentInstanceBootMode | legacy-bios |||
||| EbsOptimized | False |||
||| EnaSupport | True |||
||| Hypervisor | xen |||
||| ImageId | ami-0e4f2a1b8f55a8acd |||
||| InstanceId | i-02e3734f64e2df541 |||
||| InstanceType | t3.medium |||
||| KeyName | |||
||| LaunchTime | 2025-02-06T02:03:53+00:00 |||
||| PlatformDetails | Linux/UNIX |||
||| PrivateDnsName | ip-192-168-1-100.ap-northeast-2.compute.internal |||
||| PrivateIpAddress | 192.168.1.100 |||
||| PublicDnsName | ec2-3-39-254-196.ap-northeast-2.compute.amazonaws.com |||
||| PublicIpAddress | 3.39.254.196 |||
||| RootDeviceName | /dev/xvda |||
||| RootDeviceType | ebs |||
||| SourceDestCheck | True |||
||| StateTransitionReason | |||
||| SubnetId | subnet-0d6e865cbb265b1b7 |||
||| UsageOperation | RunInstances |||
||| UsageOperationUpdateTime | 2025-02-06T02:03:53+00:00 |||
||| VirtualizationType | hvm |||
||| VpcId | vpc-052abc90394ed7474 |||
||+--------------------------------------------+---------------------------------------------------------------------------------------------+||
✅ VPC + Subnet 정보 확인
## 계정 정보 제외를 위해 grep -v 계정 ID 옵션 추가
## VPC 정보 확인
$ aws ec2 describe-vpcs --filters "Name=tag:Name, Values=$CLUSTER_NAME-VPC" --output yaml | grep -v {arn ID}
Vpcs:
- BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.0.0/16
CidrBlockAssociationSet:
- AssociationId: vpc-cidr-assoc-082e769a61ace39cf
CidrBlock: 192.168.0.0/16
CidrBlockState:
State: associated
DhcpOptionsId: dopt-0268c590de28b1eac
InstanceTenancy: default
IsDefault: false
State: available
Tags:
- Key: aws:cloudformation:stack-id
- Key: Name
Value: myeks-VPC
- Key: aws:cloudformation:logical-id
Value: EksVPC
- Key: aws:cloudformation:stack-name
Value: myeks
VpcId: vpc-052abc90394ed7474
==================================================================================================================================
## Subent 정보 확인
$ aws ec2 describe-subnets --filters "Name=vpc-id,Values=$VPCID" --output yaml | grep -v {arn ID}
Subnets:
- AssignIpv6AddressOnCreation: false
AvailabilityZone: ap-northeast-2a
AvailabilityZoneId: apne2-az1
AvailableIpAddressCount: 250
BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.1.0/24
DefaultForAz: false
EnableDns64: false
Ipv6CidrBlockAssociationSet: []
Ipv6Native: false
MapCustomerOwnedIpOnLaunch: false
MapPublicIpOnLaunch: true
PrivateDnsNameOptionsOnLaunch:
EnableResourceNameDnsAAAARecord: false
EnableResourceNameDnsARecord: false
HostnameType: ip-name
State: available
SubnetId: subnet-0d6e865cbb265b1b7
Tags:
- Key: aws:cloudformation:stack-id
- Key: kubernetes.io/role/elb
Value: '1'
- Key: Name
Value: myeks-PublicSubnet1
- Key: aws:cloudformation:logical-id
Value: PublicSubnet1
- Key: aws:cloudformation:stack-name
Value: myeks
VpcId: vpc-052abc90394ed7474
- AssignIpv6AddressOnCreation: false
AvailabilityZone: ap-northeast-2c
AvailabilityZoneId: apne2-az3
AvailableIpAddressCount: 251
BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.2.0/24
DefaultForAz: false
EnableDns64: false
Ipv6CidrBlockAssociationSet: []
Ipv6Native: false
MapCustomerOwnedIpOnLaunch: false
MapPublicIpOnLaunch: true
PrivateDnsNameOptionsOnLaunch:
EnableResourceNameDnsAAAARecord: false
EnableResourceNameDnsARecord: false
HostnameType: ip-name
State: available
SubnetId: subnet-0fc561673d1d4a362
Tags:
- Key: Name
Value: myeks-PublicSubnet2
- Key: aws:cloudformation:stack-name
Value: myeks
- Key: kubernetes.io/role/elb
Value: '1'
- Key: aws:cloudformation:logical-id
Value: PublicSubnet2
- Key: aws:cloudformation:stack-id
VpcId: vpc-052abc90394ed7474
- AssignIpv6AddressOnCreation: false
AvailabilityZone: ap-northeast-2c
AvailabilityZoneId: apne2-az3
AvailableIpAddressCount: 251
BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.4.0/24
DefaultForAz: false
EnableDns64: false
Ipv6CidrBlockAssociationSet: []
Ipv6Native: false
MapCustomerOwnedIpOnLaunch: false
MapPublicIpOnLaunch: false
PrivateDnsNameOptionsOnLaunch:
EnableResourceNameDnsAAAARecord: false
EnableResourceNameDnsARecord: false
HostnameType: ip-name
State: available
SubnetId: subnet-01fa7e48594769839
Tags:
- Key: aws:cloudformation:logical-id
Value: PrivateSubnet2
- Key: Name
Value: myeks-PrivateSubnet2
- Key: aws:cloudformation:stack-name
Value: myeks
- Key: aws:cloudformation:stack-id
- Key: kubernetes.io/role/internal-elb
Value: '1'
VpcId: vpc-052abc90394ed7474
- AssignIpv6AddressOnCreation: false
AvailabilityZone: ap-northeast-2a
AvailabilityZoneId: apne2-az1
AvailableIpAddressCount: 251
BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.3.0/24
DefaultForAz: false
EnableDns64: false
Ipv6CidrBlockAssociationSet: []
Ipv6Native: false
MapCustomerOwnedIpOnLaunch: false
MapPublicIpOnLaunch: false
PrivateDnsNameOptionsOnLaunch:
EnableResourceNameDnsAAAARecord: false
EnableResourceNameDnsARecord: false
HostnameType: ip-name
State: available
SubnetId: subnet-0f26771810ab18542
Tags:
- Key: aws:cloudformation:logical-id
Value: PrivateSubnet1
- Key: aws:cloudformation:stack-name
Value: myeks
- Key: aws:cloudformation:stack-id
- Key: Name
Value: myeks-PrivateSubnet1
- Key: kubernetes.io/role/internal-elb
Value: '1'
VpcId: vpc-052abc90394ed7474
==================================================================================================================================
## 퍼블릭 Subnet 정보 확인
$ aws ec2 describe-subnets --filters Name=tag:Name,Values="$CLUSTER_NAME-PublicSubnet1" --output yaml | grep -v {arn ID}
Subnets:
- AssignIpv6AddressOnCreation: false
AvailabilityZone: ap-northeast-2a
AvailabilityZoneId: apne2-az1
AvailableIpAddressCount: 250
BlockPublicAccessStates:
InternetGatewayBlockMode: off
CidrBlock: 192.168.1.0/24
DefaultForAz: false
EnableDns64: false
Ipv6CidrBlockAssociationSet: []
Ipv6Native: false
MapCustomerOwnedIpOnLaunch: false
MapPublicIpOnLaunch: true
PrivateDnsNameOptionsOnLaunch:
EnableResourceNameDnsAAAARecord: false
EnableResourceNameDnsARecord: false
HostnameType: ip-name
State: available
SubnetId: subnet-0d6e865cbb265b1b7
Tags:
- Key: aws:cloudformation:stack-id
- Key: kubernetes.io/role/elb
Value: '1'
- Key: Name
Value: myeks-PublicSubnet1
- Key: aws:cloudformation:logical-id
Value: PublicSubnet1
- Key: aws:cloudformation:stack-name
Value: myeks
VpcId: vpc-052abc90394ed7474
==================================================================================================================================
## 퍼블릭 Subnet ID 확인
$ aws ec2 describe-subnets --filters Name=tag:Name,Values="$CLUSTER_NAME-PublicSubnet1" --query "Subnets[0].[SubnetId]" --output text
✅ 위에서 수행한 명령어를 기반으로 Public Subnet 1,2 Env 설정
export PubSubnet1=$(aws ec2 describe-subnets --filters Name=tag:Name,Values="$CLUSTER_NAME-PublicSubnet1" --query "Subnets[0].[SubnetId]" --output text)
export PubSubnet2=$(aws ec2 describe-subnets --filters Name=tag:Name,Values="$CLUSTER_NAME-PublicSubnet2" --query "Subnets[0].[SubnetId]" --output text)
echo "export PubSubnet1=$PubSubnet1" >> /etc/profile
echo "export PubSubnet2=$PubSubnet2" >> /etc/profile
echo $PubSubnet1
echo $PubSubnet2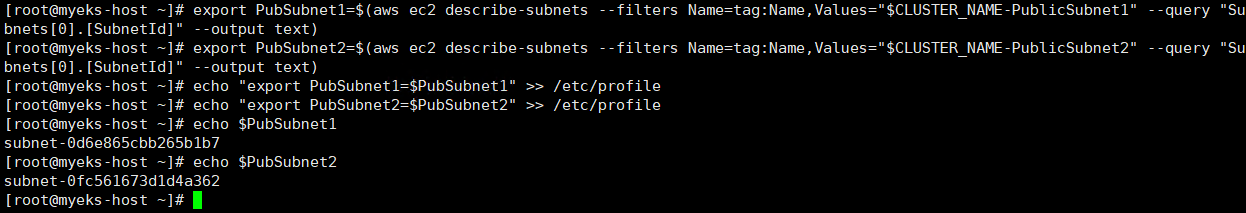
✅ EKS 버전별 사용 가능한 Addon 정보 확인
#!/bin/bash
echo "Enter K8s Version"
read version
aws eks describe-addon-versions --kubernetes-version $version --query 'addons[].{MarketplaceProductUrl: marketplaceInformation.productUrl, Name: addonName, Owner: owner Publisher: publisher, Type: type}' --output text | awk '{print $2}' | while read list; do echo ">> Addon Name: $list <<"; aws eks describe-addon-versions --addon-name $list | jq -r '
.addons[] |
.addonVersions[] |
select(.architecture[] | index("amd64")) |
[.addonVersion, (.compatibilities[] | .clusterVersion), (.compatibilities[] | .defaultVersion)] |
@tsv'; done
- EKSCTL 사용
## EKSCTL Usage
$ eksctl help
============================================
Usage: eksctl [command] [flags]
Commands:
eksctl anywhere EKS anywhere
eksctl associate Associate resources with a cluster
eksctl completion Generates shell completion scripts for bash, zsh or fish
eksctl create Create resource(s)
eksctl delete Delete resource(s)
eksctl deregister Deregister a non-EKS cluster
eksctl disassociate Disassociate resources from a cluster
eksctl drain Drain resource(s)
eksctl enable Enable features in a cluster
eksctl get Get resource(s)
eksctl help Help about any command
eksctl info Output the version of eksctl, kubectl and OS info
eksctl register Register a non-EKS cluster
eksctl scale Scale resources(s)
eksctl set Set values
eksctl unset Unset values
eksctl update Update resource(s)
eksctl upgrade Upgrade resource(s)
eksctl utils Various utils
eksctl version Output the version of eksctl
$ eksctl create
============================================
Create resource(s)
Usage: eksctl create [flags]
Commands:
eksctl create accessentry Create access entries
eksctl create addon Create an Addon
eksctl create cluster Create a cluster
eksctl create fargateprofile Create a Fargate profile
eksctl create iamidentitymapping Create an IAM identity mapping
eksctl create iamserviceaccount Create an iamserviceaccount - AWS IAM role bound to a Kubernetes service account
eksctl create nodegroup Create a nodegroup
eksctl create podidentityassociation Create a pod identity association
Common flags:
-C, --color string toggle colorized logs (valid options: true, false, fabulous) (default "true")
-d, --dumpLogs dump logs to disk on failure if set to true
-h, --help help for this command
-v, --verbose int set log level, use 0 to silence, 4 for debugging and 5 for debugging with AWS debug logging (default 3)
Use 'eksctl create [command] --help' for more information about a command.
For detailed docs go to https://eksctl.io/
============================================
$ eksctl create cluster --help ## cluster 생성 설명
$ eksctl create nodegroup --help ## nodegroup 생성 설명
$ eksctl utils schma | jq ## 사용 가능한 스키마 설명
EKSCTL --dry-run 옵션으로 항목 살펴보기
## NodeGroup 없이 Cluster만 생성
$ eksctl create cluster --name myeks --region=ap-northeast-2 --without-nodegroup --dry-run | yh
accessConfig:
authenticationMode: API_AND_CONFIG_MAP
addonsConfig: {}
apiVersion: eksctl.io/v1alpha5
availabilityZones:
- ap-northeast-2b
- ap-northeast-2a
- ap-northeast-2d
cloudWatch:
clusterLogging: {}
...
vpc:
autoAllocateIPv6: false
cidr: 192.168.0.0/16
clusterEndpoints:
privateAccess: false
publicAccess: true
manageSharedNodeSecurityGroupRules: true
nat:
gateway: Single
## NodeGroup 없이 Cluster 생성 + AZ 지정
$ eksctl create cluster --name myeks --region=ap-northeast-2 --without-nodegroup --zones=ap-northeast-2a,ap-northeast-2c --dry-run | yh
accessConfig:
authenticationMode: API_AND_CONFIG_MAP
addonsConfig: {}
apiVersion: eksctl.io/v1alpha5
availabilityZones:
- ap-northeast-2a
- ap-northeast-2c
cloudWatch:
clusterLogging: {}
...
vpc:
autoAllocateIPv6: false
cidr: 192.168.0.0/16
clusterEndpoints:
privateAccess: false
publicAccess: true
manageSharedNodeSecurityGroupRules: true
nat:
gateway: Single
## EKS 클러스터 생성 + 관리형 노드그룹 생성 + 가용 영역 지정 + VPC CIDR 지정
$ eksctl create cluster --name myeks --region=ap-northeast-2 --nodegroup-name=mynodegroup --node-type=t3.medium --node-volume-size=30 \
--zones=ap-northeast-2a,ap-northeast-2c --vpc-cidr=172.20.0.0/16 --dry-run | yh
...
availabilityZones:
- ap-northeast-2a
- ap-northeast-2c
cloudWatch:
clusterLogging: {}
iam:
vpcResourceControllerPolicy: true
withOIDC: false
kind: ClusterConfig
kubernetesNetworkConfig:
ipFamily: IPv4
managedNodeGroups:
- amiFamily: AmazonLinux2
desiredCapacity: 2
disableIMDSv1: true
disablePodIMDS: false
...
instanceType: t3.medium
labels:
alpha.eksctl.io/cluster-name: myeks
alpha.eksctl.io/nodegroup-name: mynodegroup
maxSize: 2
minSize: 2
name: mynodegroup
privateNetworking: false
releaseVersion: ""
securityGroups:
withLocal: null
withShared: null
ssh:
allow: false
publicKeyPath: ""
tags:
alpha.eksctl.io/nodegroup-name: mynodegroup
alpha.eksctl.io/nodegroup-type: managed
volumeIOPS: 3000
volumeSize: 30
volumeThroughput: 125
volumeType: gp3
metadata:
name: myeks
region: ap-northeast-2
version: "1.30"
...
vpc:
autoAllocateIPv6: false
cidr: 172.20.0.0/16
clusterEndpoints:
privateAccess: false
publicAccess: true
manageSharedNodeSecurityGroupRules: true
nat:
gateway: Single
## EKS 클러스터 생성 + 관리형 노드 그룹 생성(OS Type, 이름, node 인스턴스 타입, EBS 볼륨 사이즈, SSH 허용) + 가용 영역 지정 + VPC CIDR
$ eksctl create cluster --name myeks --region=ap-northeast-2 --nodegroup-name=mynodegroup --node-type=t3.medium --node-volume-size=30 \
--zones=ap-northeast-2a,ap-northeast-2c --vpc-cidr=172.20.0.0/16 --ssh-access --node-ami-family Ubuntu2004 --dry-run | yh
...
availabilityZones:
- ap-northeast-2a
- ap-northeast-2c
...
managedNodeGroups:
- amiFamily: Ubuntu2004
...
instanceSelector: {}
instanceType: t3.medium
...
maxSize: 2
minSize: 2
name: mynodegroup
...
ssh:
allow: true
publicKeyPath: ~/.ssh/id_rsa.pub
tags:
alpha.eksctl.io/nodegroup-name: mynodegroup
alpha.eksctl.io/nodegroup-type: managed
volumeIOPS: 3000
volumeSize: 30
volumeThroughput: 125
volumeType: gp3
...
vpc:
autoAllocateIPv6: false
cidr: 172.20.0.0/16
clusterEndpoints:
privateAccess: false
publicAccess: true
manageSharedNodeSecurityGroupRules: true
nat:
gateway: Single
EKSCTL로 진짜 배포하기
## bastion 서버 생성 시 설정한 변수 확인
$ echo $AWS_DEFAULT_REGION ; echo $CLUSTER_NAME ; echo $VPCID ; echo $PubSubnet1,$PubSubnet2
ap-northeast-2
myeks
vpc-052abc90394ed7474
subnet-0d6e865cbb265b1b7,subnet-0fc561673d1d4a362
## EC2 생성 모니터링 - EKS 배포 시 Worker node 생성에 대한 모니터링
$ while true; do aws ec2 describe-instances --query "Reservations[*].Instances[*].{PublicIPAdd:PublicIpAddress,PrivateIPAdd:PrivateIpAddress,InstanceName:Tags[?Key=='Name']|[0].Value,Status:State.Name}" --filters Name=instance-state-name,Values=running --output text ; echo "------------------------------" ; sleep 1; done
aws ec2 describe-instances --query "Reservations[*].Instances[*].{PublicIPAdd:PublicIpAddress,PrivateIPAdd:PrivateIpAddress,InstanceName:Tags[?Key=='Name']|[0].Value,Status:State.Name}" --filters Name=instance-state-name,Values=running --output table
## EKS 배포 시작
## -v, --verbose int set log level, use 0 to silence, 4 for debugging and 5 for debugging with AWS debug logging (default 3)
$ eksctl create cluster --name $CLUSTER_NAME --region=$AWS_DEFAULT_REGION --nodegroup-name=$CLUSTER_NAME-nodegroup --node-type=t3.medium --node-volume-size=30 --vpc-public-subnets "$PubSubnet1,$PubSubnet2" --version 1.31 --ssh-access --external-dns-access --verbose 4
✅ EKSCTL로 배포를 시작하면 CloudFormation에 stack이 생성되어 콘솔에서 확인할 수 있고,
CLI 창에서도 확인이 가능합니다.
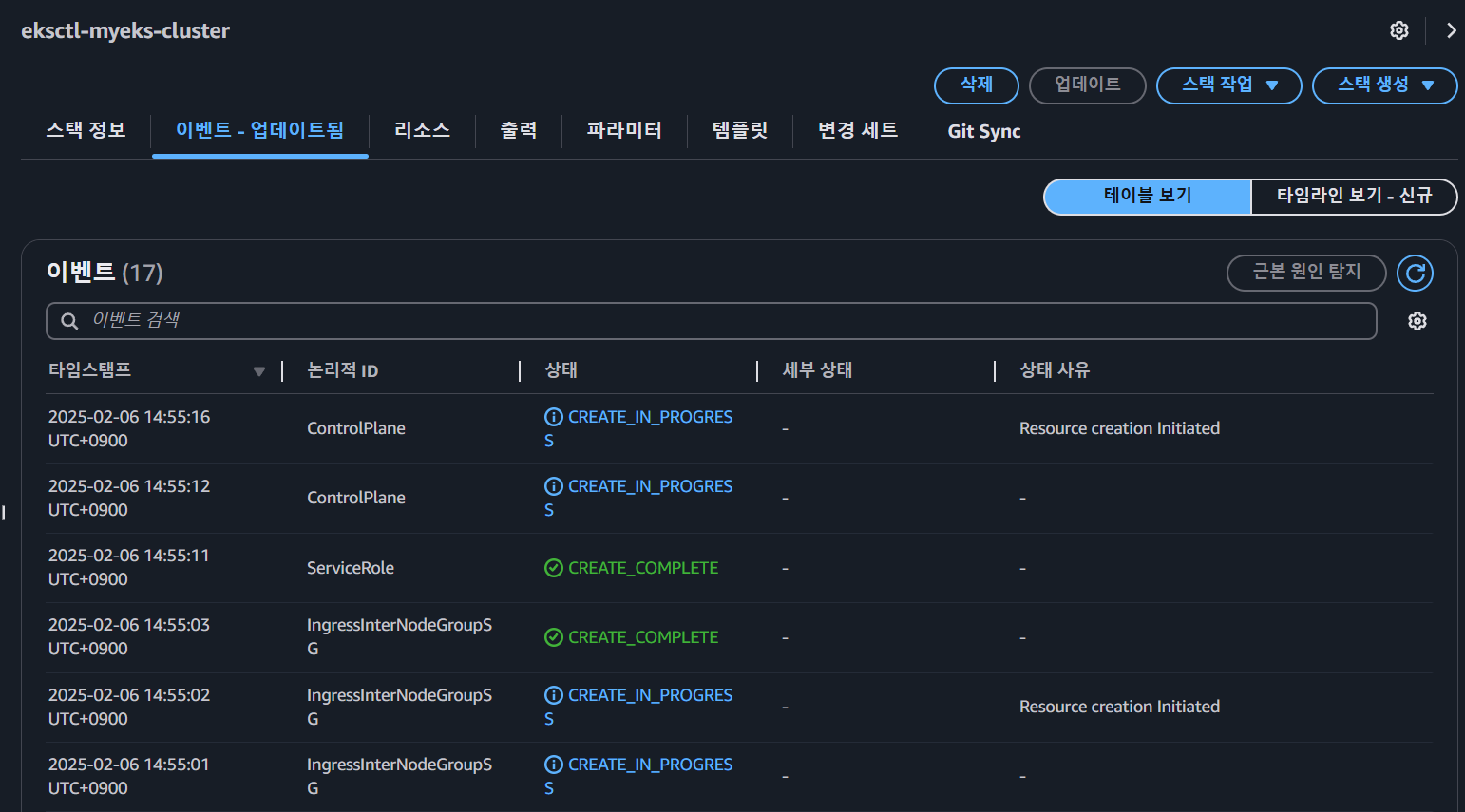
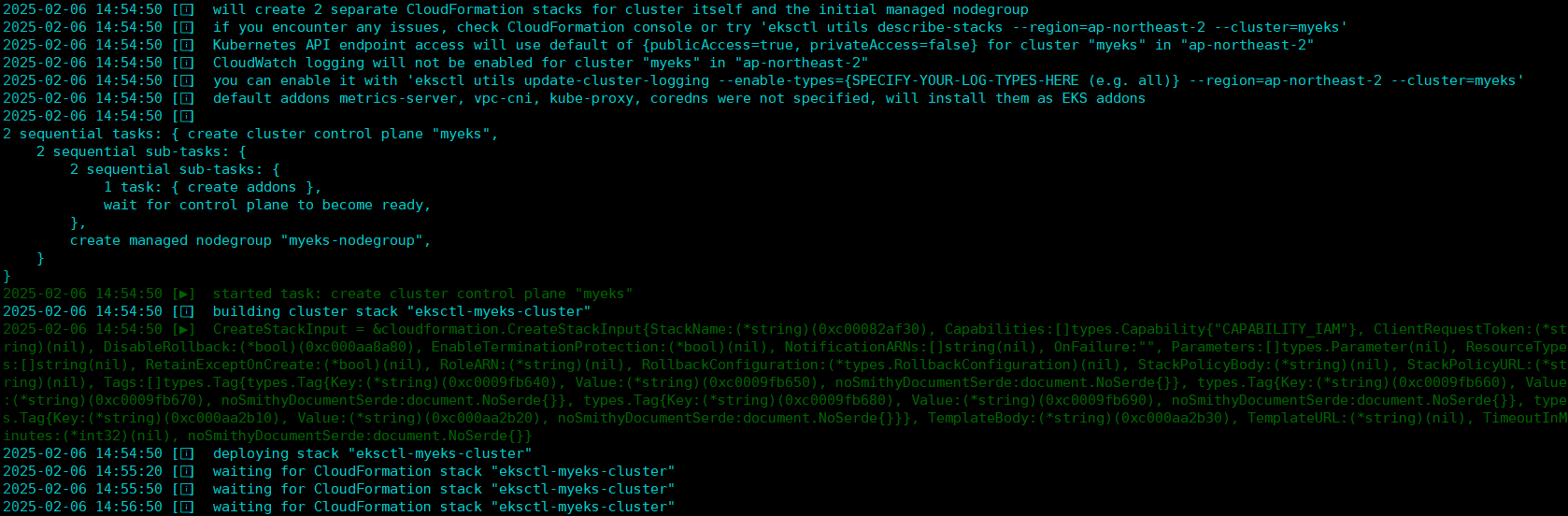
모니터링에서도 Worker Node Instance가 Running 상태로 추가된 것을 확인할 수 있습니다.
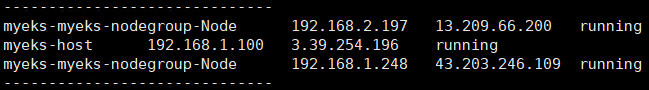
✅ Cluster 생성 확인
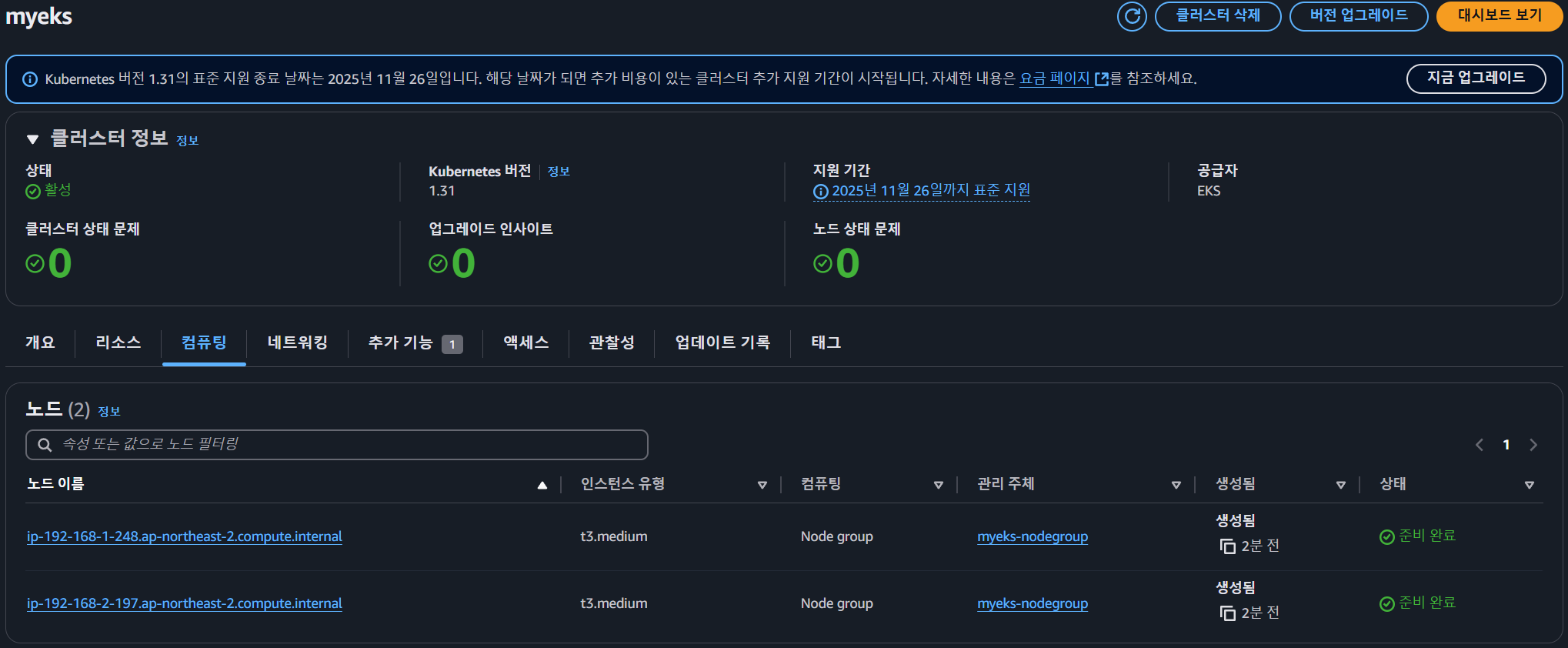
## node 리스트 조회
$ k get node
NAME STATUS ROLES AGE VERSION
ip-192-168-1-248.ap-northeast-2.compute.internal Ready <none> 3m5s v1.31.4-eks-aeac579
ip-192-168-2-197.ap-northeast-2.compute.internal Ready <none> 3m8s v1.31.4-eks-aeac579
## node 정보 조회
$ k describe node
Name: ip-192-168-1-248.ap-northeast-2.compute.internal
Roles: <none>
Labels: alpha.eksctl.io/cluster-name=myeks
alpha.eksctl.io/nodegroup-name=myeks-nodegroup
beta.kubernetes.io/arch=amd64
beta.kubernetes.io/instance-type=t3.medium
beta.kubernetes.io/os=linux
eks.amazonaws.com/capacityType=ON_DEMAND
eks.amazonaws.com/nodegroup=myeks-nodegroup
eks.amazonaws.com/nodegroup-image=ami-005cddfeed40e0e49
eks.amazonaws.com/sourceLaunchTemplateId=lt-0a4cde36c4923ed5c
eks.amazonaws.com/sourceLaunchTemplateVersion=1
failure-domain.beta.kubernetes.io/region=ap-northeast-2
failure-domain.beta.kubernetes.io/zone=ap-northeast-2a
k8s.io/cloud-provider-aws=5553ae84a0d29114870f67bbabd07d44
kubernetes.io/arch=amd64
kubernetes.io/hostname=ip-192-168-1-248.ap-northeast-2.compute.internal
kubernetes.io/os=linux
node.kubernetes.io/instance-type=t3.medium
topology.k8s.aws/zone-id=apne2-az1
topology.kubernetes.io/region=ap-northeast-2
topology.kubernetes.io/zone=ap-northeast-2a
Annotations: alpha.kubernetes.io/provided-node-ip: 192.168.1.248
node.alpha.kubernetes.io/ttl: 0
volumes.kubernetes.io/controller-managed-attach-detach: true
CreationTimestamp: Thu, 06 Feb 2025 15:06:32 +0900
Taints: <none>
Unschedulable: false
Lease:
HolderIdentity: ip-192-168-1-248.ap-northeast-2.compute.internal
AcquireTime: <unset>
RenewTime: Thu, 06 Feb 2025 15:08:45 +0900
Conditions:
Type Status LastHeartbeatTime LastTransitionTime Reason Message
---- ------ ----------------- ------------------ ------ -------
MemoryPressure False Thu, 06 Feb 2025 15:07:02 +0900 Thu, 06 Feb 2025 15:06:31 +0900 KubeletHasSufficientMemory kubelet has sufficient memory available
DiskPressure False Thu, 06 Feb 2025 15:07:02 +0900 Thu, 06 Feb 2025 15:06:31 +0900 KubeletHasNoDiskPressure kubelet has no disk pressure
PIDPressure False Thu, 06 Feb 2025 15:07:02 +0900 Thu, 06 Feb 2025 15:06:31 +0900 KubeletHasSufficientPID kubelet has sufficient PID available
Ready True Thu, 06 Feb 2025 15:07:02 +0900 Thu, 06 Feb 2025 15:06:44 +0900 KubeletReady kubelet is posting ready status
Addresses:
InternalIP: 192.168.1.248
ExternalIP: 43.203.246.109
InternalDNS: ip-192-168-1-248.ap-northeast-2.compute.internal
Hostname: ip-192-168-1-248.ap-northeast-2.compute.internal
ExternalDNS: ec2-43-203-246-109.ap-northeast-2.compute.amazonaws.com
## 설치 플러그인 확인
$ k krew list
## Cluster 정보 확인
$ k cluster-info
$ aws eks describe-cluster --name $CLUSTER_NAME | jq
## Cluster Endpoint 확인
$ aws eks describe-cluster --name $CLUSTER_NAME | jq -r .cluster.endpoint
https://EF49513DF9F9B1E8ADBB73D80593D52B.sk1.ap-northeast-2.eks.amazonaws.com
## Endpoint의 실제 리소스를 dig로 확인
$ dig +short $(aws eks describe-cluster --name $CLUSTER_NAME | jq -r .cluster.endpoint | cut -d '/' -f 3)
43.202.254.249
13.209.200.68
## aws cli로 woker node pub ip 확인
$ aws ec2 describe-instances --filter "Name=tag:Name, Values=myeks-myeks-nodegroup-Node" --query "Reservations[*].Instances[*].NetworkInterfaces[*].Association.PublicIp" --output text
## Cluster Endpoint로 version 정보 확인
$ curl -k -s $(aws eks describe-cluster --name $CLUSTER_NAME | jq -r .cluster.endpoint)/version | jq
{
"major": "1",
"minor": "31",
"gitVersion": "v1.31.5-eks-8cce635",
"gitCommit": "226ac9004c742da4a043d2fa60d191e1d8f2ea7a",
"gitTreeState": "clean",
"buildDate": "2025-01-18T07:43:58Z",
"goVersion": "go1.22.10",
"compiler": "gc",
"platform": "linux/amd64"
}
## node group 정보 확인
$ eksctl get nodegroup --cluster $CLUSTER_NAME
CLUSTER NODEGROUP STATUS CREATED MIN SIZE MAX SIZE DESIRED CAPACITY INSTANCE TYPE IMAGE ID ASG NAME TYPE
myeks myeks-nodegroup ACTIVE 2025-02-06T06:05:20Z 2 2 2 t3.medium AL2_x86_64 eks-myeks-nodegroup-88ca6cee-6e32-6258-faa2-a3bcb0015781 managed
## node의 Instance type, Capacitytype, Zone 정보 확인
## label-columns를 사용하면 label의 key값으로 조회해서 value를 출력 열에 추가해 표시합니다.
$ k get node --label-columns=node.kubernetes.io/instance-type,eks.amazoneaws.com/capacityType.topology.kubernetes.io/zone
NAME STATUS ROLES AGE VERSION INSTANCE-TYPE ZONE
ip-192-168-1-248.ap-northeast-2.compute.internal Ready <none> 39m v1.31.4-eks-aeac579 t3.medium
ip-192-168-2-197.ap-northeast-2.compute.internal Ready <none> 39m v1.31.4-eks-aeac579 t3.medium
## aws cli의 get-token으로 kubernetes의 인증 정보도 확인해 봅니다.
$ aws eks get-token --cluster-name $CLUSTER_NAME --region $AWS_DEFAULT_REGION
## Pod 정보 확인
### kube-system 관련 pod 확인
$ k get pod -n kube-system
NAME READY STATUS RESTARTS AGE
aws-node-dd68v 2/2 Running 0 61m
aws-node-r4pp6 2/2 Running 0 61m
coredns-9b5bc9468-lmcc9 1/1 Running 0 65m
coredns-9b5bc9468-tzwmh 1/1 Running 0 65m
kube-proxy-d2lff 1/1 Running 0 61m
kube-proxy-ll5gs 1/1 Running 0 61m
metrics-server-86bbfd75bb-fnncw 1/1 Running 0 65m
metrics-server-86bbfd75bb-xsrjk 1/1 Running 0 65m
### node 메트릭 확인
$ k top node
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
ip-192-168-1-248.ap-northeast-2.compute.internal 31m 1% 518Mi 15%
ip-192-168-2-197.ap-northeast-2.compute.internal 31m 1% 519Mi 15%
### pod 메트릭 확인
$ k top pod -A
NAMESPACE NAME CPU(cores) MEMORY(bytes)
kube-system aws-node-dd68v 4m 60Mi
kube-system aws-node-r4pp6 4m 61Mi
kube-system coredns-9b5bc9468-lmcc9 1m 12Mi
kube-system coredns-9b5bc9468-tzwmh 1m 12Mi
kube-system kube-proxy-d2lff 1m 11Mi
kube-system kube-proxy-ll5gs 1m 11Mi
kube-system metrics-server-86bbfd75bb-fnncw 3m 17Mi
kube-system metrics-server-86bbfd75bb-xsrjk 3m 17Mi
## 모든 파드의 컨테이너 이미지 정보 확인
$ k get pods --all-namespaces -o jsonpath="{.items[*].spec.containers[*].image}" | tr -s '[[:space:]]' '\n' | sort | uniq -c
--all-namespaces: 모든 네임스페이스에서 파드를 조회
-o jsonpath="{.items[*].spec.containers[*].image}": jsonpath 표현식을 사용하여 각 파드의 컨테이너 이미지 경로를 출력
tr -s '[[:space:]]' '\n': jsonpath로 출력된 내용을 tr로 전달하고, space(공백)을 줄바꿈으로 변환하여 한 줄에 하나씩 출력
728x90
'Cloud > AWS' 카테고리의 다른 글
| [AWS] EKS 설치 및 기본 사용 (3) (0) | 2025.02.08 |
|---|---|
| [AWS] EKS 설치 및 기본 사용 (2) (0) | 2025.02.07 |
| [AWS] EKS에 대하여 (0) | 2025.02.05 |
| [AWS] Terraform으로 Karpenter 설치하고 노드 증설하기 (2) | 2024.11.05 |
| [AWS] EKS 생성 (by terraform) (0) | 2024.07.17 |
