728x90
선언형(멱등성) 알아보기
멱등성(idempotency) : 동일한 작업을 여러 번 수행하여도 결과가 달라지지 않는 것을 의미합니다.
예시)
# 첫 번째 실행 - 성공
k create deployment my-webs --image=gcr.io/google-samples/kubernetes-bootcamp:v1 --replicas=3
# 두 번째 실행 - 에러 발생
Error from server (AlreadyExists): deployments.apps "my-webs" already exists# apply를 사용한 경우
k apply deployment my-webs --image=gcr.io/google-samples/kubernetes-bootcamp:v1 --replicas=3 # 정상 생성
k apply deployment my-webs --image=gcr.io/google-samples/kubernetes-bootcamp:v1 --replicas=3 # 변경 사항 없음
create의 경우는 에러가 발생했으므로 멱등하지 않지만, apply의 경우 두번째 실행해서 에러가 발생하지 않고,
변경 사항이 없었기 때문에 멱등하다고 볼 수 있습니다.
## deploy 생성 (Pod 3개)
$ k create deployment my-webs --image=gcr.io/google-samples/kubernetes-bootcamp:v1 --replicas=3
## 생성 pod 확인
$ k get pod
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-2zxdw 1/1 Running 0 32s
my-webs-56cd645dc9-ktq4v 1/1 Running 0 32s
my-webs-56cd645dc9-v6sfr 1/1 Running 0 32s
## 파드 증가 및 감소
$ k scale deploy my-webs --replicas=6 && k get pod
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-2zxdw 1/1 Running 0 116s
my-webs-56cd645dc9-j5bgd 1/1 Running 0 44s
my-webs-56cd645dc9-ktq4v 1/1 Running 0 116s
my-webs-56cd645dc9-lzwps 1/1 Running 0 44s
my-webs-56cd645dc9-v6sfr 1/1 Running 0 116s
my-webs-56cd645dc9-v96cc 1/1 Running 0 44s
$ k scale deploy my-webs --replicas=3
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-2zxdw 1/1 Running 0 2m10s
my-webs-56cd645dc9-j5bgd 1/1 Terminating 0 58s
my-webs-56cd645dc9-ktq4v 1/1 Running 0 2m10s
my-webs-56cd645dc9-lzwps 1/1 Terminating 0 58s
my-webs-56cd645dc9-v6sfr 1/1 Running 0 2m10s
my-webs-56cd645dc9-v96cc 1/1 Terminating 0 58s
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-2zxdw 1/1 Running 0 2m51s
my-webs-56cd645dc9-ktq4v 1/1 Running 0 2m51s
my-webs-56cd645dc9-v6sfr 1/1 Running 0 2m51s
## pod 전체 삭제
$ k delete pod --all
pod "my-webs-56cd645dc9-2zxdw" deleted
pod "my-webs-56cd645dc9-ktq4v" deleted
pod "my-webs-56cd645dc9-v6sfr" deleted
## 진행 상황
# pod는 삭제는 되었지만 deploy에 설정된 desired 값으로 인해 새로운 파드 3개가 생성됨
# Replicas: 3 desired | 3 updated | 3 total | 3 available | 0 unavailable
$ k get pod
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-2zxdw 1/1 Terminating 0 3m34s
my-webs-56cd645dc9-kpbpg 1/1 Running 0 13s
my-webs-56cd645dc9-ktq4v 1/1 Terminating 0 3m34s
my-webs-56cd645dc9-ltrd9 1/1 Running 0 13s
my-webs-56cd645dc9-njhtt 1/1 Running 0 13s
my-webs-56cd645dc9-v6sfr 1/1 Terminating 0 3m34s
$ k get pod
NAME READY STATUS RESTARTS AGE
my-webs-56cd645dc9-kpbpg 1/1 Running 0 47s
my-webs-56cd645dc9-ltrd9 1/1 Running 0 47s
my-webs-56cd645dc9-njhtt 1/1 Running 0 47s
노드에 배포된 컨테이너 정보 확인
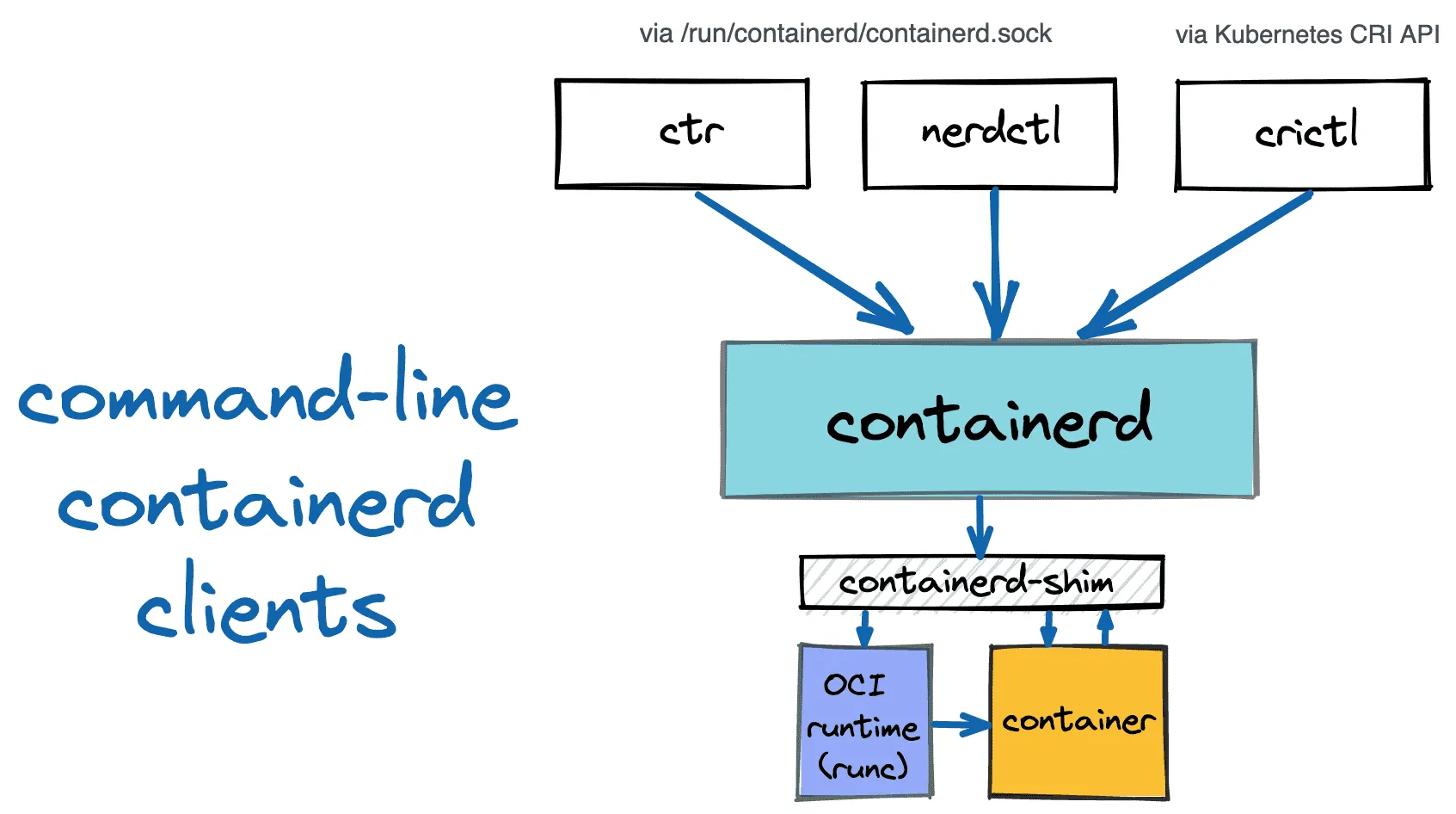
## ctr 버전 확인
$ ssh ec2-user@$N1 ctr --version
ctr github.com/containerd/containerd 1.7.25
## ctr help
$ ssh ec2-user@$N1 ctr
## 네임스페이스 확인
$ ssh ec2-user@$N1 sudo ctr ns list
NAME LABELS
k8s.io
## 어떤 프로세스에서 네임스페이스를 사용하고 있는지 확인
$ ssh ec2-user@$N1 sudo ps -auxf | grep containerd
root 2982 0.1 0.3 1238536 14376 ? Sl 05:28 0:09 /usr/bin/containerd-shim-runc-v2 -namespace k8s.io -id 9946459496a4b30d325774f95e7bde65c3158e9fe421451d80108faaa041b79a -address /run/containerd/containerd.sock
root 2983 0.0 0.3 1238536 14324 ? Sl 05:28 0:02 /usr/bin/containerd-shim-runc-v2 -namespace k8s.io -id 792d839f7cd2ff426b7feeef74a96097e962483f8607da7a49c5cf8b95445780 -address /run/containerd/containerd.sock
root 3627 0.0 0.3 1238280 14480 ? Sl 05:28 0:02 /usr/bin/containerd-shim-runc-v2 -namespace k8s.io -id 13c263e35cc9bd6f6a2b7ee5ee92bf9c38dc0804de993e7d4fcb75ab0ff0dd7c -address /run/containerd/containerd.sock
## 컨테이너 리스트 확인
$ for i in $N1 $N2; do echo ">> node $i <<"; ssh ec2-user@$i sudo ctr -n k8s.io container list; echo; done
CONTAINER IMAGE RUNTIME
28d470d9078b1b3968bfcc3560c092f1d5d1f156608a90b86f00d286e1d8ecf8 602401143452.dkr.ecr.ap-northeast-2.amazonaws.com/eks/pause:3.5 io.containerd.runc.v2
## 컨테이너 이미지 확인
$ for i in $N1, $N2; do echo ">> node $i <<"; ssh ec2-user@$i sudo ctr -n k8s.io image list --quiet; echo; done
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni-init:v1.19.0
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni-init:v1.19.0-eksbuild.1
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni-init:v1.19.2
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni-init:v1.19.2-eksbuild.1
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni:v1.19.0
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni:v1.19.0-eksbuild.1
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni:v1.19.2
066635153087.dkr.ecr.il-central-1.amazonaws.com/amazon-k8s-cni:v1.19.2-eksbuild.1
066635153087.dkr.ecr.il-central-1.amazonaws.com/eks/kube-proxy:v1.31.2-minimal-eksbuild.3
066635153087.dkr.ecr.il-central-1.amazonaws.com/eks/kube-proxy:v1.31.3-minimal-eksbuild.2
121268973566.dkr.ecr.ap-southeast-7.amazonaws.com/amazon-k8s-cni-init:v1.19.0
121268973566.dkr.ecr.ap-southeast-7.amazonaws.com/amazon-k8s-cni-init:v1.19.0-eksbuild.1
121268973566.dkr.ecr.ap-southeast-7.amazonaws.com/amazon-k8s-cni-init:v1.19.2
121268973566.dkr.ecr.ap-southeast-7.amazonaws.com/amazon-k8s-cni-init:v1.19.2-eksbuild.1
121268973566.dkr.ecr.ap-southeast-7.amazonaws.com/amazon-k8s-cni:v1.19.0
...
## 태스크 리스트 확인
$ for i in $N1, $N2; do echo ">> node $i <<"; ssh ec2-user@$i sudo ctr -n k8s.io task list; echo; done
TASK PID STATUS
e12df9e301b3d9538b6e9705ba1d5cb7dcd041840d5c9a0b93bc8b73b206e391 3355 RUNNING
c6ddb013b813e8b9e9cd946122b9e3cc66072c30cf4b8ad3a76c15a87bd70f55 3723 RUNNING
c0ce02949b3ac70c3e13f46aa23d54f29100bd3a437d88a7873fe9e1e8cb9353 3884 RUNNING
f59c0e66bbc0696414acb5648465ba636cd1417497158518a62d5fa2466dce34 3967 RUNNING
5a431d740bee745d2b27c5b8ba802d04139eb77e0e5c80be7668c55104db6637 3109 RUNNING
821ea44197613de30a7270bc6c62779d8f2270f3e5d6310d154abd4059af7727 3023 RUNNING
28d470d9078b1b3968bfcc3560c092f1d5d1f156608a90b86f00d286e1d8ecf8 3675 RUNNING
7d862ffce2b3409d4f9c530fa6923ed77bb28f8b0b18a24406de801d530bd4f8 3739 RUNNING
6f6c6277dc64b07c0659e57f5662659073ba228cdd92c17215f6095961f3bee7 3015 RUNNING
ec3886b21aa6555e78dc06d8994d13541361b3821efd72408a6e6e25f79c22bd 3490 RUNNING
daf91e701a0a2e3f8a4ee00e06b1d2934ea249e336af4ac6c8eab65833a5bcf7 3646 RUNNING
## 태스크의 프로세스 확인
$ ssh ec2-user@$N2 ps -c 3109
PID CLS PRI TTY STAT TIME COMMAND
3109 TS 19 ? Ssl 0:00 kube-proxy --v=2 --config=/var/lib/kube-proxy-config/config --hostname-override=ip-192-168-2-247.ap-northeast-2.compute.internal
Private ECR 사용하기
## ECR 인증 및 레포 로그인
$ aws ecr get-login-password --region ap-northeast-2 | docker login --username AWS --password-stdin {Account ID}.dkr.ecr.ap-northeast-2.amazonaws.com
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
## ECR Repo 정보 확인
$ aws ecr describe-registry --region ap-northeast-2 | jq
$ aws ecr describe-repositories --region ap-northeast-2 | jq
## ECR 생성
$ aws ecr create-repository --repository-name ssungz/nginx --region ap-northeast-2
## 생성 확인
$ aws ecr describe-repositories --output yaml
- createdAt: '2025-02-08T16:06:30.821000+09:00'
encryptionConfiguration:
encryptionType: AES256
imageScanningConfiguration:
scanOnPush: false
imageTagMutability: MUTABLE
registryId: ''
repositoryArn: arn:aws:ecr:ap-northeast-2:{accoutID}:repository/ssungz/nginx
repositoryName: ssungz/nginx
repositoryUri: {accoutID}.dkr.ecr.ap-northeast-2.amazonaws.com/ssungz/nginx
## docker 이미지 생성
$ docker pull nginx:alpine
$ docker images
$ docker tag nginx:alpine {accoutID}.dkr.ecr.ap-northeast-2.amazonaws.com/ssungz/nginx:latest
$ docker push {accoutID}.dkr.ecr.ap-northeast-2.amazonaws.com/ssungz/nginx:latest
## POD 실행
$ k run mynginx --image {accoutID}.dkr.ecr.ap-northeast-2.amazonaws.com/ssungz/nginx:latest
## ECR 업로드 이미지 삭제
$ aws ecr batch-delete-image --repository-name ssungz/nginx --image-ids imageTag=latest --region ap-northeast-2
## ECR 레포 삭제
$ aws ecr delete-repository --repository-name ssungz/nginx --force --region ap-northeast-2
## 레포 삭제 확인
$ $ aws ecr describe-repositories --output yaml
관리형 노드에 노드 추가 및 삭제
## 실행 중 ec2 리스트 조회
$ while true; do aws ec2 describe-instances --query "Reservations[*].Instances[*].{PublicIPAdd:PublicIpAddress,PrivateIPAdd:PrivateIpAddress,InstanceName:Tags[?Key=='Name']|[0].Value,Status:State.Name}" --filters Name=instance-state-name,Values=running --output text ; echo "------------------------------" ; sleep 1; done
## eksctl로 노드 그룹 정보 확인
$ eksctl get nodegroup --cluster $CLUSTER_NAME --name $CLUSTER_NAME-nodegroup
CLUSTER NODEGROUP STATUS CREATED MIN SIZE MAX SIZE DESIRED CAPACITY INSTANCE TYPE IMAGE ID ASG NAME TYPE
myeks myeks-nodegroup ACTIVE 2025-02-08T05:27:08Z 2 2 2 t3.medium AL2_x86_64 eks-myeks-nodegroup-ceca7203-4c01-e0de-7f1f-ee089142b4b0 managed
## 노드 개수를 2 > 3 으로 scale out
## 기본 3개, 최소 3개, 최대 6개 설정
$ eksctl scale nodegroup --cluster $CLUSTER_NAME --name $CLUSTER_NAME-nodegroup --nodes 3 --nodes-min 3 --nodes-max 6
## 모니터링 세션에서 node 개수 증가 확인
myeks-myeks-nodegroup-Node 192.168.2.247 52.79.243.174 running
myeks-myeks-nodegroup-Node 192.168.2.99 13.209.50.254 running
myeks-myeks-nodegroup-Node 192.168.1.150 3.36.114.90 running
## Cluster에서 신규 worker 조인 확인
$ k get node -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
ip-192-168-1-150.ap-northeast-2.compute.internal Ready <none> 114m v1.31.4-eks-aeac579 192.168.1.150 3.36.114.90 Amazon Linux 2 5.10.233-223.887.amzn2.x86_64 containerd://1.7.25
ip-192-168-2-247.ap-northeast-2.compute.internal Ready <none> 114m v1.31.4-eks-aeac579 192.168.2.247 52.79.243.174 Amazon Linux 2 5.10.233-223.887.amzn2.x86_64 containerd://1.7.25
ip-192-168-2-99.ap-northeast-2.compute.internal Ready <none> 27s v1.31.4-eks-aeac579 192.168.2.99 13.209.50.254 Amazon Linux 2 5.10.233-223.887.amzn2.x86_64 containerd://1.7.25
## node 개수 축소
# eksctl 사용 예제
$ eksctl scale nodegroup --cluster $CLUSTER_NAME --name $CLUSTER_NAME-nodegroup --nodes 2 --nodes-min 2
# aws cli 사용 예제
$ aws eks update-nodegroup-config --cluster-name $CLUSTER_NAME --nodegroup-name $CLUSTER_NAME-nodegroup --scaling-config minSize=2,maxSize=2,desiredSize=2
노드 축소 시 사용한 aws cli와 eksctl의 차이
[aws cli]
- EKS 관리형 노드 그룹에서만 사용 가능
- 즉각적 반영이 아니며, ASG 설정 변경과 내부 동작 후 적용
[eksctl]
- 즉시 노드 개수 변경
- 빠른 조정이 필요할 경우 사용
- 관리형 노드 그룹에서 사용 가능
728x90
'Cloud > AWS' 카테고리의 다른 글
| [AWS] EKS Networkings (2) (0) | 2025.02.16 |
|---|---|
| [AWS] EKS Networkings (1) (0) | 2025.02.15 |
| [AWS] EKS 설치 및 기본 사용 (2) (0) | 2025.02.07 |
| [AWS] EKS 설치 및 기본 사용 (1) (0) | 2025.02.06 |
| [AWS] EKS에 대하여 (0) | 2025.02.05 |
